National Security Agency, Fort George Meade
If it’s an international telephone call, fax, or e-mail that travels by satellite or microwave link over any part of its journey; it may well be intercepted by the National Security Agency (NSA). The same thing goes for cell phone calls (there are orbiting NSA satellites that do nothing but intercept cell phone calls), radio transmissions, and other electronic communications that cross international borders and domestic communications can be, and have been, monitored with equal ease. NSA has the most advanced computers in the world, and their text and speech recognition software scans all intercepted communications for key words and phrases; if they detect any of these, then the entire communication is analyzed. And don’t think that using e-mail encryption or telephone scrambling gives you security NSA can easily crack such encryption, and using it only makes the NSA more curious about you.
In the spring of 1999, reports began to appear in the media about a new system called “Echelon,” a network of spy satellites and worldwide listening posts run by the National Security Agency (NSA). The May 27, 1999 issues of both Business Week and The New York Times carried stories about Echelon, and its sinister ability to intercept telephone calls (including cell phones), faxes, e-mail, and radio signals and then analyze their contents with powerful supercomputers to look for key words or phrases. As Business Week to\6 its readers, “Just get used to the fact Big Brother is listening.”
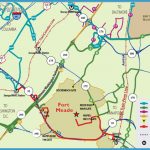
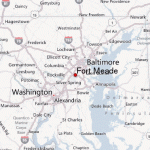
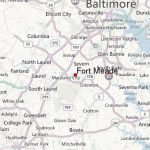
Fort George Meade Maryland Map Photo Gallery
The reaction of those who had been following the NSA for years was a bit different it was “so what else is new?” The only thing noteworthy about the Echelon revelations was that we finally know the code name of the NSA’s worldwide snooping system and the extent to which foreign nations, particularly the British, are involved. But the functions of Echelon have been carried on for decades. The only thing that has changed has been the NSA’s capabilities for widespread eavesdropping. As computer hardware and software have improved, so have the efficiency and pervasiveness of NSA’s snooping. In fact, it’s safest today to assume that any communication you make via electronic means by phone, fax, the Internet, radio, etc. may be intercepted and analyzed by the National Security Agency.
The NSA doesn’t, to be the best of our knowledge, actually install wiretaps on phone lines. It doesn’t have to, because most electronic communications today involve some wireless links. Cell phone and long-distance calls use satellites; many local calls use microwave relays beyond your local switching office. And when something is sent via wireless, the NSA is listening to it, storing it, and processing it. If there is something in the communication that catches the NSA’s interest, like a certain word or phrase or the use of encryption, the NSA analyzes it to see if it has any “national security” implications. If the analysis yields something suspicious, or if the NSA can’t figure out what the communication is about, the parties involved may be targets of more intensive surveillance, including possible wiretaps authorized by the Foreign Intelligence Surveillance Act (FISA) Court (see entry in DISTRICT OF COLUMBIA).
While it is the NSA’s interception of telephone calls and faxes that upset most people, the NSA also tracks everything sent electronically, including e-mail, financial transactions (like stock trades and credit card sales), travel reservations, etc. If it involves a wireless link at some point along the way, the NSA is trying to intercept and analyze it. In addition, recent reports have claimed that the NSA is tapping into undersea cables and network access points that local Internet service providers (ISPs) use to connect to the Internet.
In addition to its own signal intercept facilities, the NSA also serves as a central clearinghouse for all intercepts by the military and the various civilian agencies of the federal government. The results of all signals intelligence activities by the U.S. Army, Navy, Air Force, and Coast Guard are all sent to the NSA for its processing and analysis. The same thing happens with signals intercepted by the FBI, Customs Service, Drug Enforcement Administration, the Federal Communications Commission, etc. If it’s anything that appears remotely connected to “national security” (or if the intercepting agency can’t figure out what it is), it winds up in the NSA’s lap.
To keep track of all the stuff it intercepts and receives from other agencies, the NSA has developed what has to be the most impressive (and scary) computing capabilities in the world. Its main headquarters at Fort George Meade houses perhaps the most awesome collection of physical and human computing resources anywhere. The NSA has what is reported to be the second most powerful collection of supercomputers in the world (and that might be an understatement). Its computer scientists and programmers have developed incredibly sophisticated software capable of analyzing digitized phone calls and documents to find certain words or phrases or patterns in the use of words. When these are found, the file is then more intensively analyzed, including the use of human analysts.
Make no mistake about it: despite some recent attempts to “humanize” it, the NSA is a scary outfit. For years, it was so secret that its very name was classified (the joke was that “NSA” stood for “no such agency”). That cult of secrecy still pervades NSA. The details of its budgets and special access programs (SAPs) are unknown to all but a handful of members of Congress, and even they only have a cursory knowledge of what those involve. In fact, the size of the NSA’s annual budget and number of employees is not accurately known because so much of its funding is hidden in SAPs. Estimates of the NSA’s budget range from $2.8 billion to over $10 billion and its number of employees has been pegged at anywhere between 38,000 to 52,000.
The NSA was not created by an act of Congress, and no statute establishes the agency or defines the permissible scope of its activities (this is in sharp contrast to the CIA, which was created by an act of Congress and thus has clearly defined missions and accountability). The NSA came into being on November 4, 1952, as a result of a National Security Council Intelligence Directive issued by President Harry Truman under the authority of the National Security Act of 1947. President Truman’s directive consolidated the various signal interception and analysis activities of the U.S. government, including those of the military, under the umbrella of the NSA. The directive itself was classified Top Secret until the 1970s.
The NSA’s operating authority is to gather “foreign intelligence” for the purposes of “national security.” However, those terms have never been precisely defined and are open to broad and creative interpretation. No law has ever been enacted by Congress to prohibit the NSA from engaging in any activity; however, Congress has enacted numerous laws prohibiting anyone from divulging information about the NSA or its activities.
The lax definitions of “foreign intelligence” and “national security” resulted in the NSA turning its attention to surveillance of American citizens in the 1960s and 1970s. Senate hearings chaired in 1975 by Idaho Senator Frank Church revealed that the NSA began to compile “watch lists” of American citizens in 1962. The purported intent of snooping on American citizens was to determine if any “foreign powers” were lending support to the civil rights movement. These lists and surveillance efforts against Americans were greatly increased in 1967, as the NSA targeted antiwar groups and more civil rights organizations. Among the Americans whose names appeared on NSA watch lists during that era were Dr. Martin Luther King, Jane Fonda, Joan Baez, Eldridge Cleaver, and Abbie Hoffman. The NSA also began to get requests for surveillance from other government agencies, like the CIA and the Bureau of Narcotics and Dangerous Drugs (the forerunner of today’s Drug Enforcement Administration), that were prohibited by law from conducting such surveillance.
The NSA’s program of domestic spying was finally ended by Attorney General Elliott Richardson in October 1973, as the rapidly-unraveling Watergate scandal threatened to expose it. In the wake of Watergate, NSA Director Lew Allen finally revealed the NSA’s surveillance efforts against Americans to the Church committee in 1975. This was accompanied by promises to establish safeguards to prevent such abuses in the future.
One such safeguard put into place after the Church hearings was to protect the privacy of U.S. citizens who were not targeted or otherwise under suspicion but had been a party to an intercepted communication. In such cases, the U.S. citizen is supposed to be referred to simply as “American Citizen” in all summaries, transcripts, and records of the communication. However, there have been numerous reports that the NSA can get around this self-imposed restriction by allowing a foreign partner, such as the Canadians or British, to do the analysis of the communication.
The NSA still fights Congressional efforts to control its activities. In 1999, the House Permanent Select Committee on Intelligence attempted to investigate how the NSA handled intercepted communications involving American citizens. The committee requested legal opinions, decisional memoranda, and policy guidelines the NSA used to handle intercepted phone, fax, and e-mail communications from citizens. The NSA responded by claiming an attorney/client privilege between the NSA director and its general counsel, thus exempting the requested documents from Congressional review (this was the same tactic President Nixon tried with John Dean during the Watergate scandal). Even right-wing Republicans on the committee were outraged by the NSA’s response. Representative Bob Barr (R-Georgia), a former CIA analyst, called the NSA claim “bogus” and said it was an attempt to “deny the chairman and committee members proper information with which to carry out their oversight responsibilities.” Despite such protests, the NSA steadfastly refused to provide the request documents and the committee could only protest in its final report.
Senator Frank Church said it best in his committee’s 1975 hearings: “I know the capacity that is there to make tyranny total in America, and we must see to it that this agency [NSA] and all agencies that possess this technology operate within the law and under proper supervision, so that we never cross over that abyss.”
The NSA in Action: A United Press International (UPI) story by Richard Sale, dated February 13, 2001, gave insights into how the NSA operates today. The article concerned the NSA’s efforts to locate Osama bin Laden through his telephone communications. Sale reported that when UPI wanted to send some information about one of bin Laden’s associates to a former CIA official using e-mail, the official replied, “My God, don’t put that in an e-mail.” The official explained that such an e-mail would get him on NSA’s watch lists and he didn’t want that to happen.
The UPI story explained that the NSA maintains computerized “dictionaries” of personal names, political groups, crime organizations, phrases, and other words. All intercepted communications are checked against these dictionaries. If there is a match between any of the dictionaries and the intercepted communication, both the sender and receiver of the communication are placed on a watch list. All future communications to and from the sender and receiver are then intercepted and analyzed. For example, suppose someone sends you an e-mail with something that matches a name, word, or phrase in one of the dictionaries. You are then placed on a NSA watch list. People you send e-mails to are added to the list; so are other people that send you e-mails. You get off the watch list when it is determined that you do not pose a threat to national security. Who determines if you no longer pose a threat to national security? The NSA. And no, the NSA does not have to tell you that you are under surveillance nor do they need any warrant to monitor your communications.
Foreign Partners: The NSA maintains close links with Canada’s Communications Security Establishment (CSE), Britain’s Government Communications Headquarters (GCHQ), Australia’s Defence Signals Directorate (DSD), and New Zealand’s Communications Security Bureau (CSB). These nations are part of a formal signals intelligence alliance with the NSA. However, the alliance is curiously one-way; the foreign agencies allow the NSA to operate listening facilities in their countries, and forward signal intercepts from their military and civilian agencies to the NSA for processing and analysis, but the NSA is under no obligation to share all of the intelligence it gathers with its partners. However, NSA generally shares enough to keep its partners happy (such as intelligence about nations in the South Pacific for Australia and New Zealand, for example) processed and analyzed by NSA’s supercomputers. In addition, the NSA has also entered into agreements with Japan and South Korea, but these nations are decidedly junior partners; they seldom get to see any intelligence gathered by the NSA or the “Anglo Alliance.” Instead, intelligence they gather is processed and returned to them; the NSA may also share it with the “Anglo Alliance” without informing Japan or South Korea.
Key Facilities: The main NSA facilities at Fort George Meade and other locations in Maryland are reported to occupy over 3.5 million square feet of space. The main NSA facilities at Fort George Meade are two high-rise office complexes and smaller support buildings, including a technical library and engineering laboratories. A 1992 report entitled List of the World’s Most Powerful Computing Sites said the NSA facilities at Fort George Meade had the world’s second most powerful collection of supercomputers; however, it is widely believed this site may be actually the world’s most powerful. In addition, the NSA leases office space at the National Business Park, across the Baltimore/Washington Parkway from the main NSA facilities, and at Airport Square Technology and Industrial Park near the Baltimore/Washington International Airport. It is believed the functions carried on at these two sites are considerably less sensitive than those at the main NSA site. It is reported that the NSA employs approximately 20,000 persons in Maryland.
NSA maintains two communications satellite interception stations in the continental United States: at Sugar Grove, West Virginia and Yakima, Washington (see entries for these facilities under those states). The Sugar Grove facility processes intercepts from communications satellites over the Atlantic while Yakima does the same for Pacific satellites. In addition, almost any military site in the United States with communications receiving equipment is a potential source of input for the NSA. It is also known that U.S. embassies and consulates abroad have signal interception capabilities; one major intelligence coup of the 1960s by the U.S. embassy in Moscow was the interception of the crude radio-telephones installed in the limousines of Politburo members. As noted earlier, intercepted communications from the military and civilian agencies are forwarded to the NSA for processing and analysis.
Overseas, the NSA and GCHQ jointly operate a mammoth listening complex at Menwith Hill, near Harrogate in Great Britain. This station mainly intercepts signals from Russia and the rest of the former Soviet bloc. Misawa Air Base at Misawa, Japan, is the NSA’s main base for eavesdropping on China and North Korea. The U.S. and Australia jointly operate a large facility at Pine Gap, Australia, that targets southeast Asia.
Getting a Look inside: The National Cryptologic Museum was opened in December 1993, adjacent to NSA headquarters. The Museum has displays of mainly historical signals intelligence and codebreaking (largely from World Wars I and II) but nothing on current activities and techniques. The museum is near the intersection of the Baltimore/Washington Parkway and Route 32; hours of operation are 9 a.m. to 4 p.m. Monday through Friday and 10 a.m. to 2 p.m. Saturday. Its phone number is (301) 688-5849.
Unusual Fact: In 1999, the NSA sent around a memo to employees banning the then-popular “Furby” toys from all NSA facilities. The “Furby,” which resembled a big-eyed, cute-faced stuffed owl, had an internal chip that allowed it to record and repeat words and phrases it heard; one of the appeals of the Furby was that it could be “taught” to speak. The NSA was worried that Furbies could overhear classified conversations, memorize them, and repeat them to unauthorized personnel. The memo advised any NSA employees who had a Furby in their office, or spotted a Furby on NSA premises, to immediately “contact their Staff Security Office for guidance.”
Getting There: From the Baltimore/Washington Parkway, take the exit for Route 32/Fort Meade. Watch for the sign for Colony 7 Road; turn onto it and follow the signs to the National Cryptographic Museum. If you continue on Route 32, you will see the main NSA headquarters between Canine and Emory roads; there will be stoplights at the intersections of these roads and Route 32. From Route 32, NSA headquarters appears to be two ordinary high-rise glass and steel office buildings; the antennas on their roofs are the only indication something unusual is going on inside them. The area is heavily patrolled, however, and people taking photographs of the buildings have been stopped by security guards.